Email Threat Intelligence: Protect Your Communication Channels
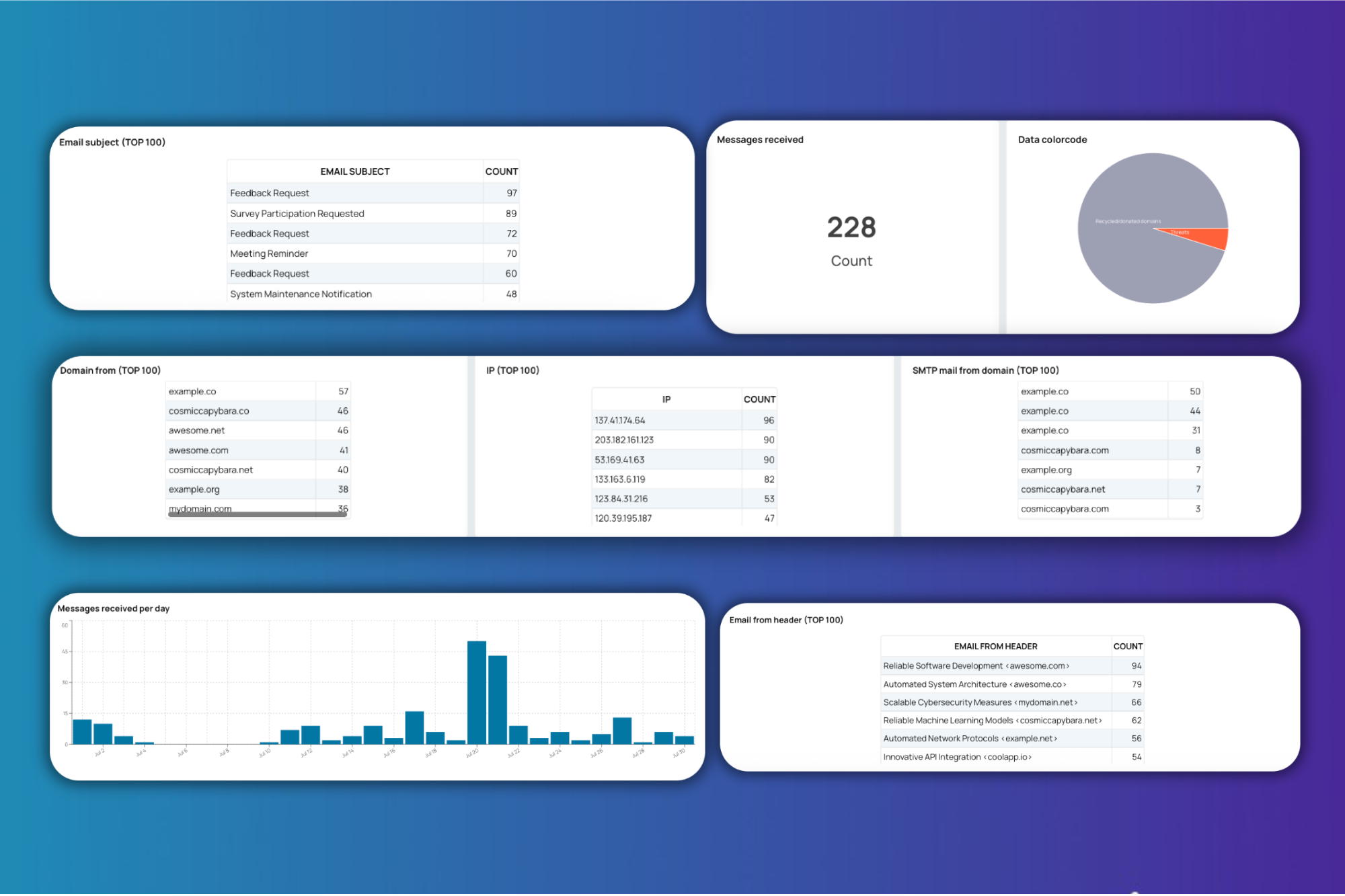
Email threats are constantly evolving, and organizations need advanced solutions to safeguard their communication systems. Explore how EmailConsul helps you stay ahead of these threats by providing robust threat intelligence services.
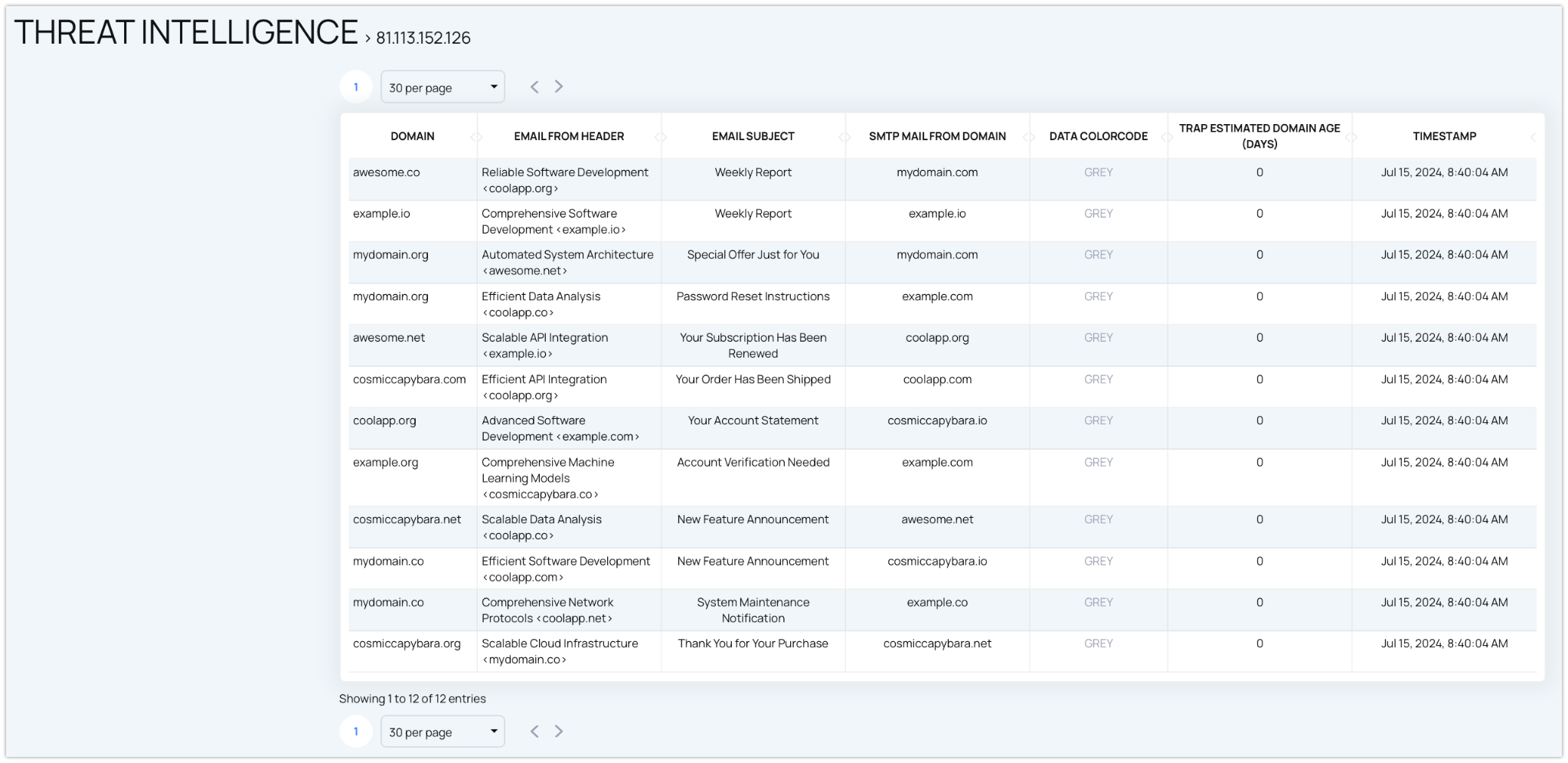
Key Components of Email Threat Intelligence
Spam Traps
- Definition: Spam traps are email addresses designed to capture unsolicited emails, often repurposed from old or abandoned addresses.
- Types:
- Pure Spam Traps: Addresses that were never used for legitimate email communication and are solely created to attract spam.
- Recycled Spam Traps: Old, inactive email addresses repurposed to identify unsolicited emails.
- Impact: Emails sent to spam traps can tarnish your sender reputation and result in blacklisting.
Old/Expired Domains
- Definition: Once-active domains that have been abandoned or expired.
- Threat: These domains can be exploited by cybercriminals to launch phishing campaigns or malicious activities under the guise of a legitimate domain.
- Monitoring: Tracking these domains can reveal potential phishing or other malicious activities.
Email Honeypots
- Definition: Systems specifically designed to attract and analyze malicious email activities, such as phishing or malware attacks.
- Purpose: By collecting data on these threats, honeypots provide deep insights into evolving tactics and enable proactive defenses.
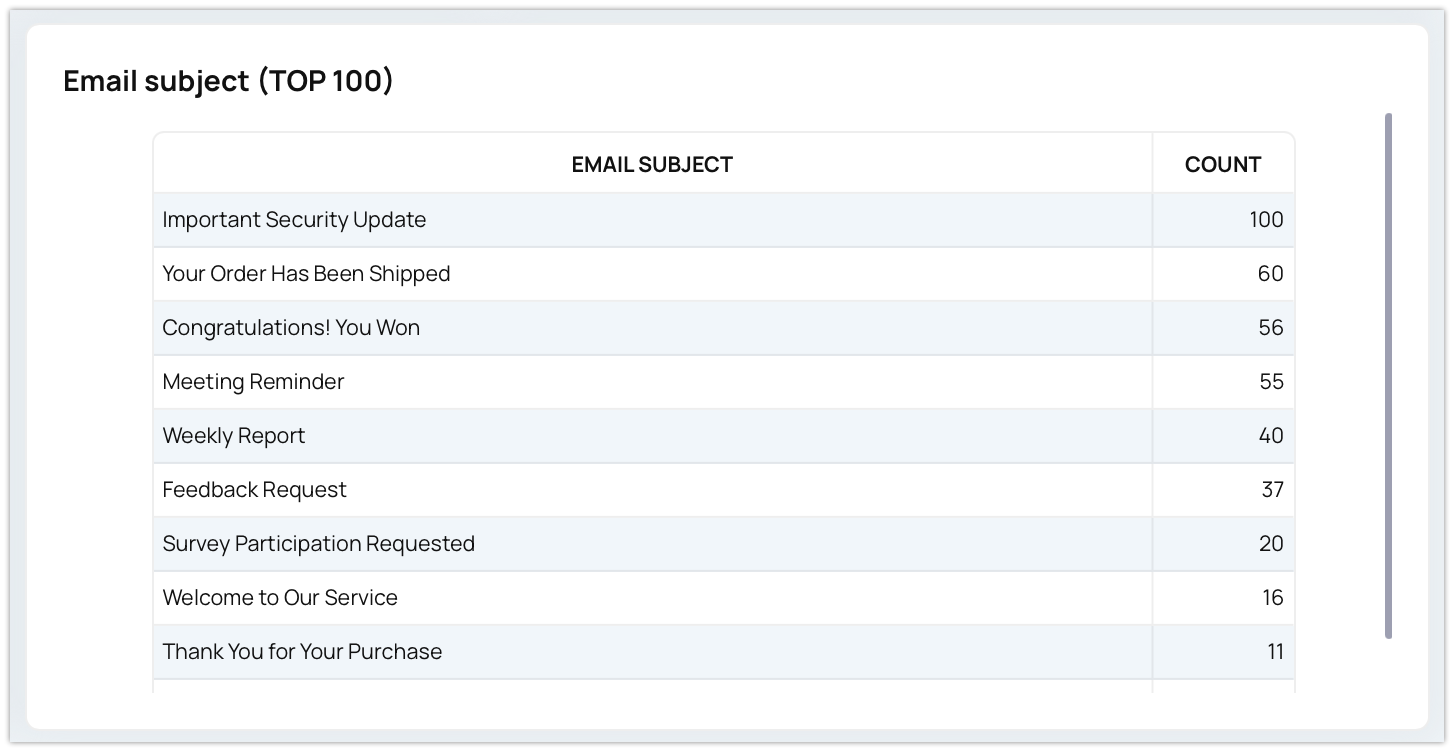
The Benefits of Using Email Threat Intelligence
Enhanced Security Posture
- Proactive Threat Identification: Threat intelligence helps organizations detect and mitigate threats before they cause damage, reinforcing overall security.
Improved Email Filtering
- Efficient Filtering: Incorporating real-time threat intelligence into your email filtering systems ensures better identification and blocking of spam, phishing, and malicious content.
Reputation Management
- Avoid Blacklisting: Monitoring spam traps and old domains prevents damage to your reputation and helps maintain a positive sender profile.
Incident Response
- Faster Recovery: Real-time insights from email threat intelligence provide critical information to respond and recover from email-based attacks effectively.
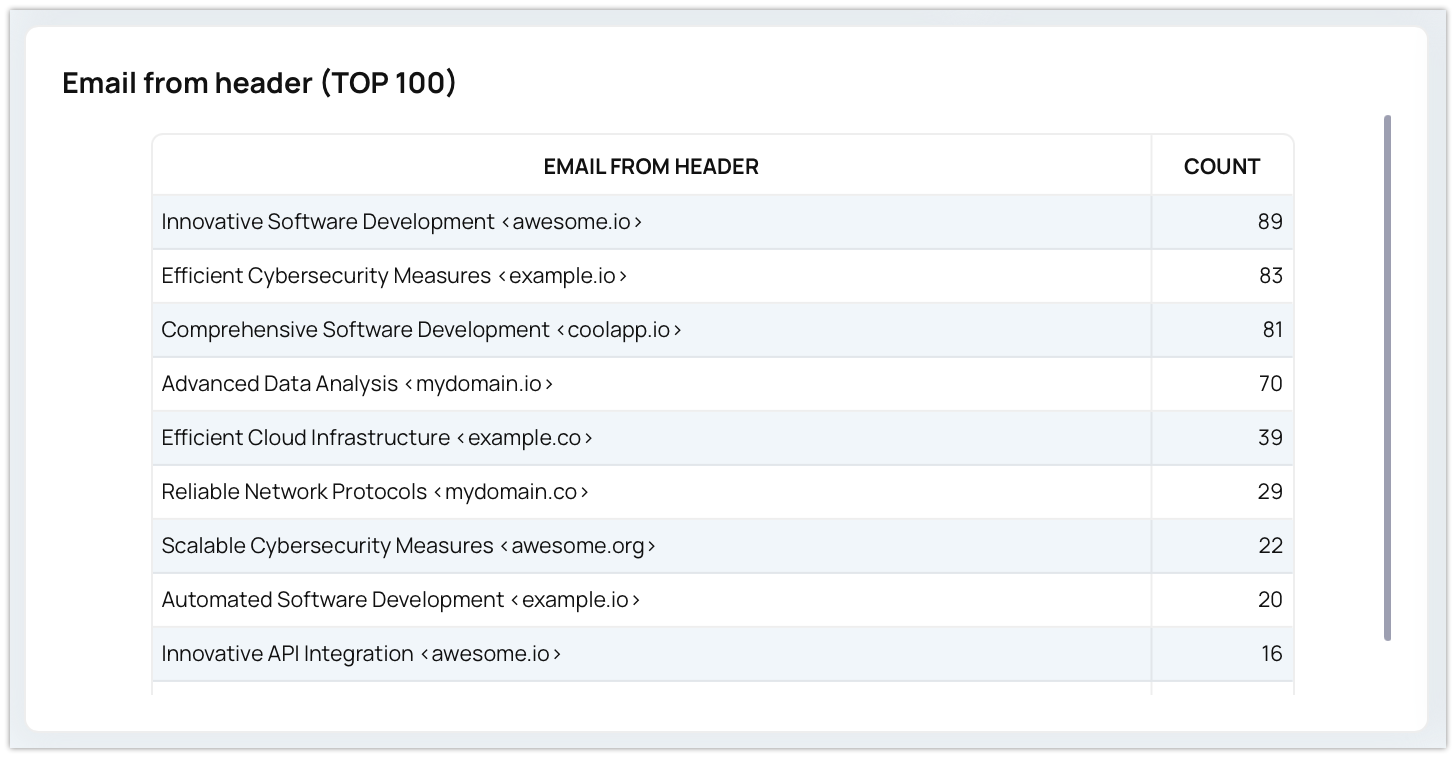
Practical Applications of Email Threat Intelligence
Blocklist Management
- Avoid Blocklisting: Proactively manage your sender reputation by identifying if your IP addresses or domains are blacklisted due to spam trap hits or other malicious activities.
Security Awareness Training
- Training with Real-Time Threats: Educate your team with the latest real-world threats, empowering them to recognize and avoid phishing and other email-based attacks.
Get Started with Email Threat Intelligence Today
Ready to strengthen your email defenses? Schedule a demo today to explore our Email Threat Intelligence solution. See how our cutting-edge service can safeguard your communication channels, ensuring comprehensive protection and peace of mind against evolving threats.
Get Started